Redqueen
Redqueen
Authors: Cornelius Aschermann, Sergej Schumilo, Tim Blazytko, Robert Gawlik, Thorsten Holz
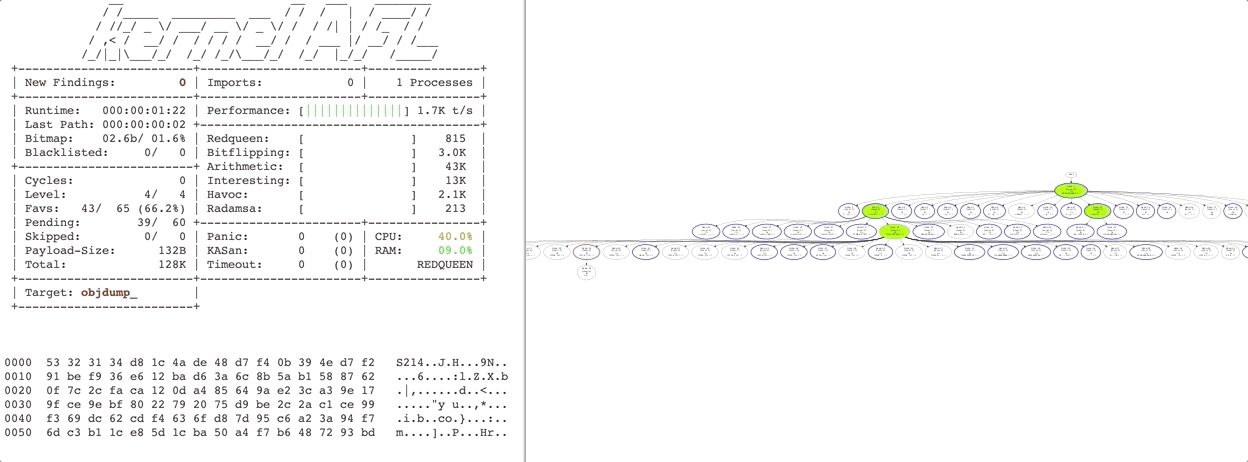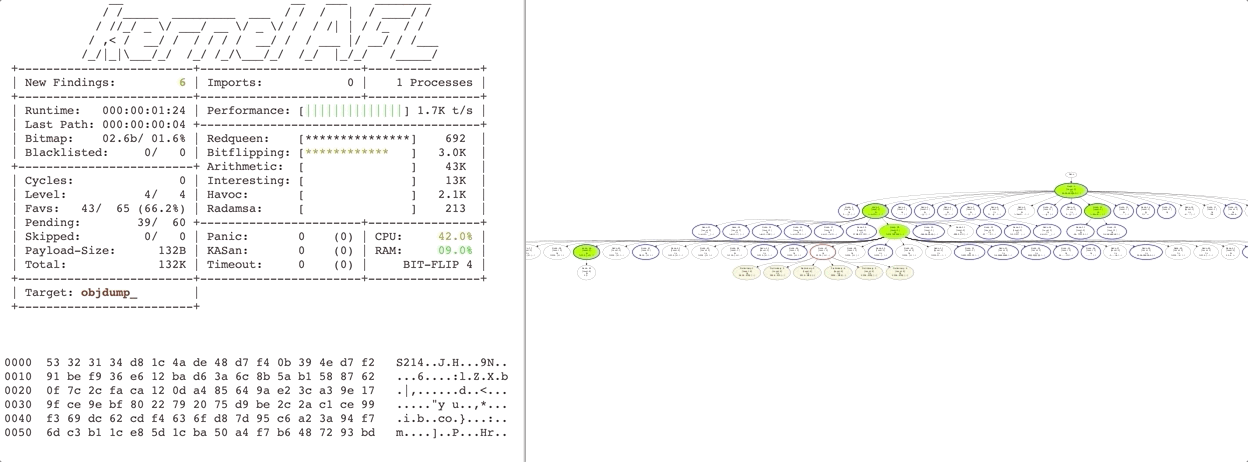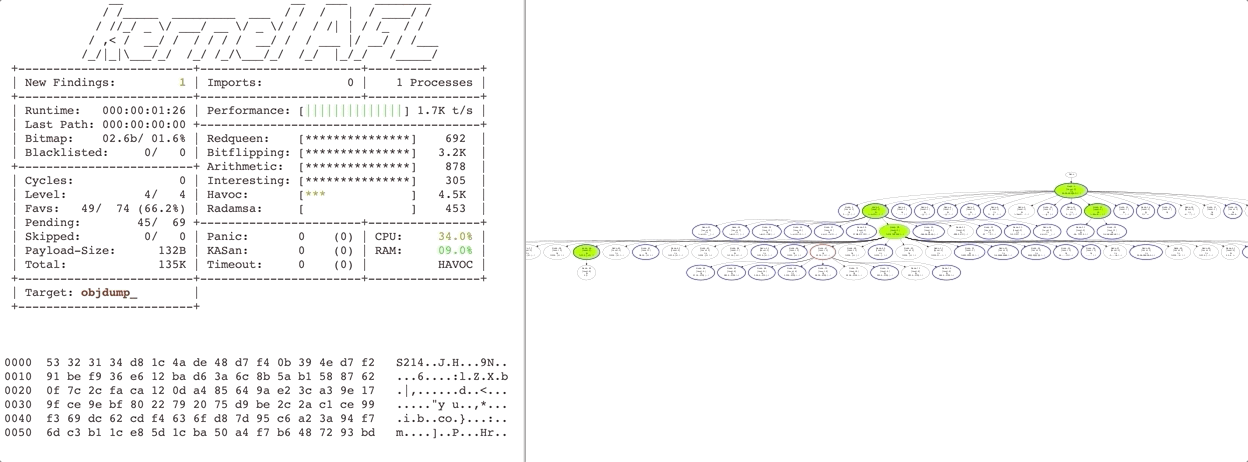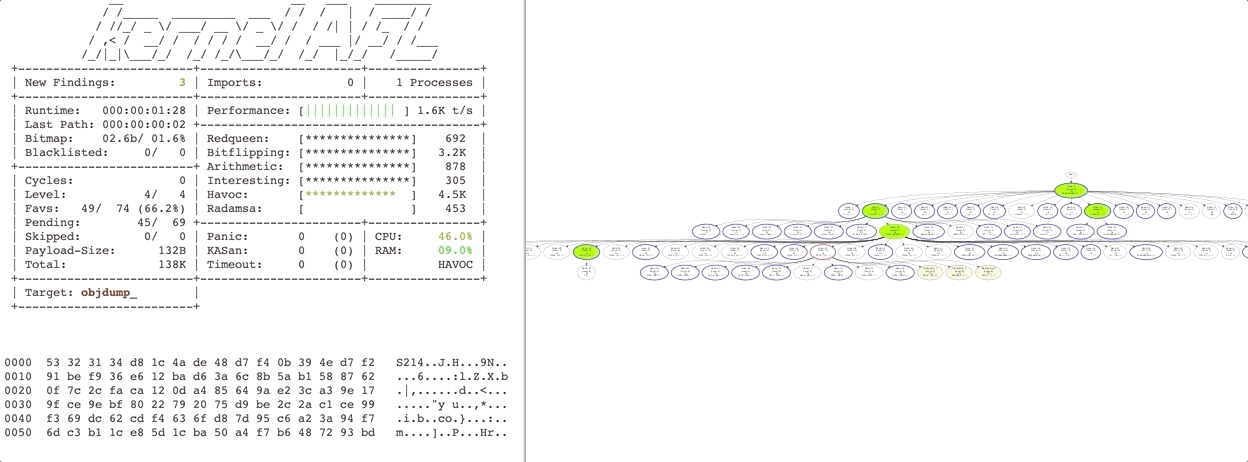
Redqueen is a fast general purpose fuzzer for x86 binary applications. It can automatically overcome checksums and magic bytes without falling back to complex and fragile program analysis techniques, such as symbolic execution. It works by observing the arguments to function calls and compare instructions via virtual machine introspection. Observed values are used to provide inputs specific mutations. More details can be found in the paper. This fuzzer is built upon kAFL and requires support for Intel VT-x as well as Intel Processor Trace. More details can be found in the paper.
The paper describing Redqueen was published at NDSS 2019. A recording of the presentation and the slides can be found here:
| Talk | Slides |
|---|---|
 |
Redqueen helped to find and report multiple bugs, including:
- binutils nm-new (CVE-2018-12641)
- binutils libiberty (CVE-2018-12697)
- binutils libiberty (CVE-2018-12698)
- binutils objdump (CVE-2018-12699)
- binutils objdump (CVE-2018-12700)
- Linux kernel 4.15.0 hfs.ko (CVE-2018-12928)
- Linux kernel 4.15.0 ntfs.ko (CVE-2018-12929)
- Linux kernel 4.15.0 ntfs.ko (CVE-2018-12930)
- Linux kernel 4.15.0 ntfs.ko (CVE-2018-12931)
- Wine (CVE-2018-12932)
- Wine (CVE-2018-12933)
- binutils cxxfilt (CVE-2018-12934)
- imagemagik (CVE-2018-12935)
- mruby (CVE-2018-14337)
- bash (CVE-2018-14566)
- xml2 (CVE-2018-14567)
- fdk-aac (CVE-2018-16747)
- fdk-aac (CVE-2018-16748)
- ImageMagick (CVE-2018-16749)
- ImageMagick (CVE-2018-16750)
- tcpdump (CVE-2018-20116)
- tcpdump (CVE-2018-20117)
- tcpdump (CVE-2018-20118)
- tcpdump (CVE-2018-20119)